
In today's rapidly evolving digital landscape, the manufacturing industry's growing reliance on software systems such as Computer-Aided Design (CAD)/Computer-Aided Manufacturing (CAM) and other specialized software underscores a pivotal shift towards increased digitization and interconnectivity. These advancements have propelled the sector forward, offering unprecedented precision, efficiency, and flexibility.
However, this digital transformation also brings to the forefront the convergences of IT and OT within manufacturing processes. This merging is a key driver of the the opportunities and vulnerabilities in the sector, highlighting the essential need for robust cybersecurity measures capable of protecting these integrated systems from cyber threats. The imperative to safeguard digital and physical assets has never been more evident, underscoring the critical need for an informed, robust and proactive approach to cybersecurity in manufacturing.
Understanding the Threat Landscape
The manufacturing sector faces a unique set of cybersecurity threats, each tailored to exploit the specific vulnerabilities of this highly digitized industry. Among these, malware, ransomware, phishing attacks, and insider threats are particularly prevalent. These vulnerabilities represent significant real-world risks that can lead to operational disruptions, financial losses, and the compromise of sensitive intellectual property. · 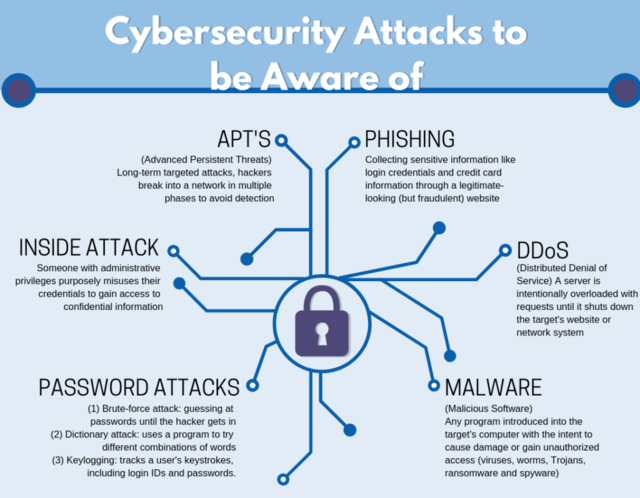
Source: Manufacturing & Technology Enterprise Center [AS2]
A striking example is that of a leading automotive manufacturer that fell victim to a ransomware attack. Cybercriminals exploited a vulnerability in the company's IT network to deploy ransomware, leading to a halt in production lines across several factories. The incident caused substantial financial losses and disrupted the global supply chain. The company responded by halting all affected systems, engaging cybersecurity experts to remove the malicious software, and working closely with law enforcement. The resolution involved restoring data from backups and reinforcing their cybersecurity measures to prevent future attacks.
Securing Manufacturing Software
Securing manufacturing software against the wide range of cyber threats requires a multifaceted approach. Here are some smart recommendations incorporating the importance of vulnerability assessments, penetration testing, and specific encryption standards:
- Regular Software Updates and Patch Management. Keeping all software systems up to date is crucial for protecting against known vulnerabilities. Regular updates and patch management practices ensure that potential entry points for cyberattacks are minimized. This includes not only the manufacturing software itself, but the operating systems and network infrastructure.
- Vulnerability Assessments and Penetration Testing. Regular vulnerability assessments and penetration testing form a critical part of the continuous monitoring and incident response strategy. These practices help identify and rectify security weaknesses before they can be exploited by attackers. Vulnerability assessments provide a broad overview of the system’s security health, while penetration testing actively exploits weaknesses to determine the real-world impact of a breach.
- Strong Authentication and Access Controls. Implementing strong passwords, multi-factor authentication (MFA), and role-based access controls can significantly limit unauthorized access to sensitive manufacturing systems. MFA adds an additional layer of security by requiring two or more verification methods.
- Network Segmentation and Firewalls. Segmenting networks and using firewalls can prevent the spread of cyber threats within an organization. By creating zones within the network, manufacturers can isolate critical software systems and data from other parts of the network, reducing the risk of lateral movement by attackers.
- Data Encryption. Encrypting sensitive data, both at rest and in transit, is essential for protecting it from unauthorized access and breaches. For the manufacturing sector, employing standards such as Advanced Encryption Standard (AES) for data at rest and Transport Layer Security (TLS) for data in transit can provide robust protection. AES is widely recognized for its strength and efficiency, while TLS ensures secure communication over a computer network.
- Employee Training and Awareness. Regular training programs empower employees to recognize and prevent cyber threats, making them an essential first line of defense against cyberattacks. This includes training on recognizing phishing attempts, safe internet practices, and the importance of reporting suspicious activities.
- Regular Backups and Recovery Plans. Maintaining regular backups and a robust disaster recovery plan can minimize downtime and operational disruption in the event of a cyber incident. These backups should be stored securely, with encryption where appropriate, and tested regularly to ensure they can be restored effectively.
- Monitoring and Incident Response. Continuous monitoring of systems for unusual activity, coupled with a well-defined incident response plan, ensures that potential threats are identified and mitigated promptly.
Incorporating these practices into a cybersecurity strategy for manufacturing software not only strengthens defenses but also aligns with industry best practices, helping to safeguard critical infrastructure and sensitive data against the evolving cyber threat landscape.
Special Considerations for CAD/CAM Software
When securing CAD/CAM software, it's imperative to address the unique challenges associated with protecting the intellectual property (IP) inherent in these files. Beyond the general cybersecurity practices, there are specific considerations for CAD/CAM systems that play a pivotal role in safeguarding sensitive design data:
- IP Protection. Protecting the intellectual property in CAD/CAM files requires a multifaceted approach. One effective strategy is the implementation of Digital Rights Management (DRM) technologies. DRM provides a robust framework to control who can access and use your digital content, including CAD/CAM files. This technology can restrict unauthorized copying, printing, and sharing of files, ensuring that sensitive design data remains within the intended user base. Additionally, DRM can enforce expiration dates on files or limit access based on user roles, providing a dynamic way to manage the lifecycle of sensitive information securely.
- Collaboration Security. The nature of manufacturing often requires sharing CAD/CAM files with external partners, suppliers, or clients. To protect these assets during collaboration, it's crucial to employ secure file-sharing platforms and protocols. These platforms should ideally integrate with your DRM solutions, allowing for seamless and secure sharing of protected files. Furthermore, it's important to establish clear guidelines and agreements with all parties involved regarding the handling, storage, and deletion of shared files to prevent accidental leaks or unauthorized access.
- Enhancing DRM with Encryption. To further reinforce the protection of CAD/CAM files, combining DRM with strong encryption protocols adds an additional layer of security. Encrypting files ensures that even if they are intercepted or accessed without authorization, the contents remain inaccessible without the appropriate decryption keys. This dual approach of DRM and encryption ensures that your intellectual property is protected not only against unauthorized access but also against potential espionage or competitive intelligence efforts.
Future Trends and Emerging Technologies
Emerging technologies such as AI and predictive analytics offer promising new ways to enhance cybersecurity in manufacturing software, enabling more proactive identification and mitigation of threats. Predictive analytics and AI can transform cybersecurity in manufacturing by enabling systems to predict potential security incidents before they occur.
For instance, AI algorithms can analyze patterns in network traffic to identify anomalies that may indicate a cyberattack, such as a sudden surge in data transfer signaling a potential data breach, or an unexpected communication attempt from a manufacturing device, which could be indicative of a malware infection. Further, AI systems can analyze historical data on software vulnerabilities and patch lifecycles to predict when a particular tool or system is becoming vulnerable, prompting early updates or replacements before an attack can happen.
The increasing use of IoT devices and edge computing in manufacturing presents both challenges and opportunities for cybersecurity, necessitating innovative approaches to protect these new frontiers. Edge computing devices can process data locally, reducing latency and bandwidth use, which is crucial for time-sensitive manufacturing processes.
When combined with robust encryption and authentication measures, these edge devices can securely communicate with central systems and other IoT devices, minimizing the risk of interception or unauthorized access. Manufacturers can deploy advanced security protocols directly onto edge devices. For example, deploying intrusion detection systems (IDS) on edge devices allows for real-time monitoring of cybersecurity threats at the point of data collection.
Similarly, implementing decentralized identity and access management solutions can ensure that only authorized devices and users can access or act upon the data processed at the edge, significantly reducing the risk of insider threats or external breaches.
As the manufacturing sector continues to evolve with the integration of AI, predictive analytics, IoT, and edge computing, so too must the approaches to cybersecurity. By leveraging these technologies, manufacturers can not only enhance the efficiency and flexibility of their operations but also significantly improve their resilience against cyber threats.
Further, with the manufacturing sector catching pace to embrace digital transformation, the importance of collaborating with a trusted cybersecurity service provider cannot be overstated. The best practices outlined above provide a foundation for securing manufacturing software systems against the evolving threat landscape. However, cybersecurity is not a one-time effort but a continuous process of adaptation and improvement. Manufacturers must remain vigilant, proactive, and ready to tackle new threats as they emerge.
[AS1]https://www.statista.com/statistics/1315805/cyber-attacks-top-industries-worldwide/
[AS2]https://mfgtec.org/cybersecurity-for-the-manufacturing-industry/






















